Microsoft Ignite day 4
At first, I was a little sceptical about day 4 as I didn’t receive that much announcements in day 3 so I thought of combining day 4 and 5. But what a day, so many announcements! Especially, check chapter 5 “Integrated Information Protection in external sharing SharePoint and OneDrive”, it’s fabulous. Here is Ignite day 4.
Index:
- Azure Blueprints
- Intune Data Warehouse
- Intune and Android Enterprise Management
- Android Management API
- Integrated Information Protection in external sharing SharePoint and OneDrive
- Experiences with going password-less
Azure Blueprints
With Azure Blueprints, announced very recently, you will get a blueprint that if you spin up a new subscription, you deploy the same policies, templates, security etc. In larger organizations, this is very helpful, you have your exact company policies spinned up in minutes! To activate this, go to the Azure Portal > Policy > Blueprints – Blueprint Definitions.
Intune Data Warehouse
At some point, if you are using Intune, you will face the problems generating reports in Intune. Fortunately, we have Intune Data Warehouse. I visited a session today at the Ignite Expo where I saw some great reports so let’s see how we actually start using Intune Data Warehouse. Go into the Azure Portal > Intune and on the right, Click “Set up Intune Data Warehouse” and click “Download Power BI file”.
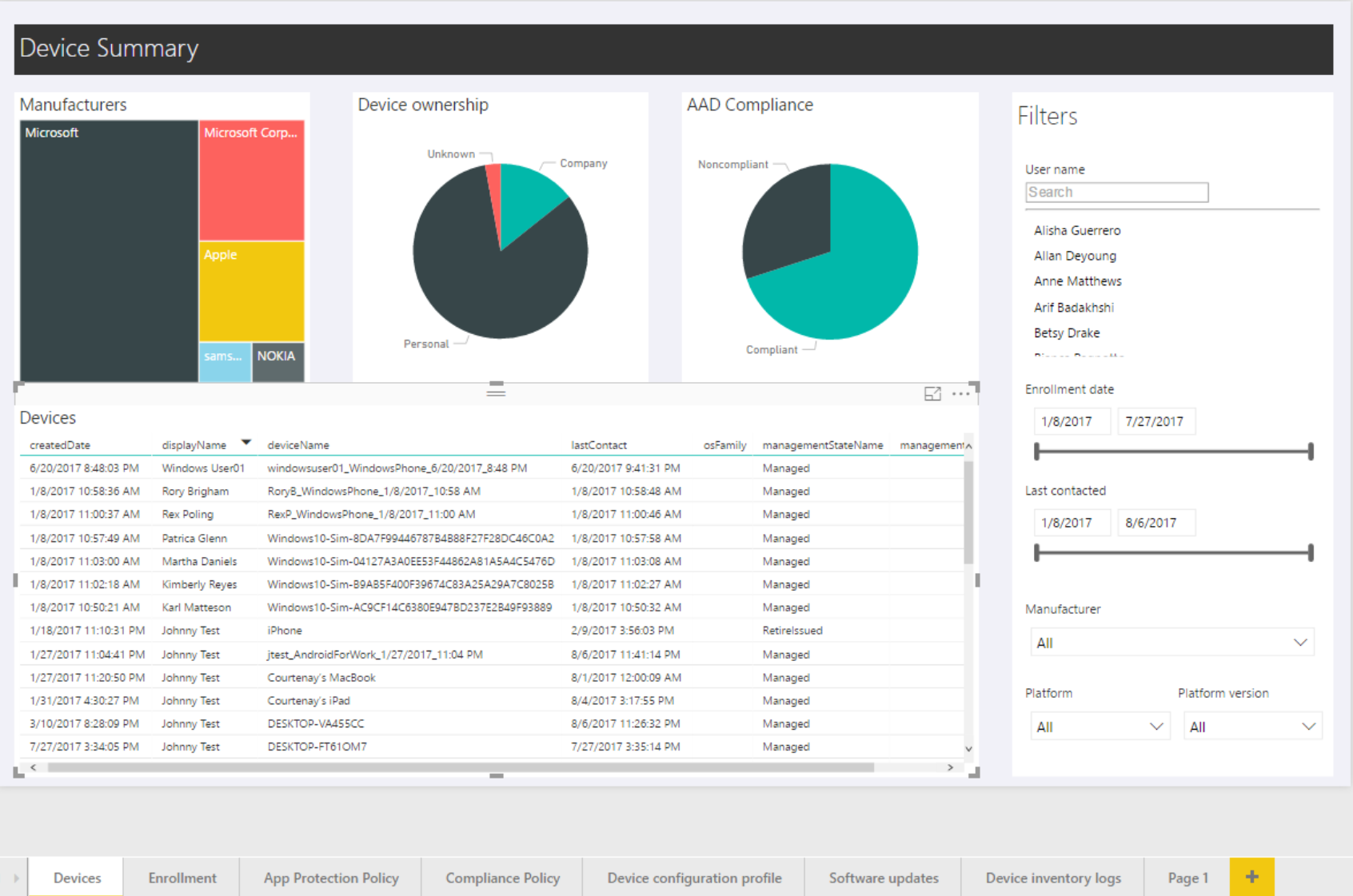
If the data is processed, you can directly start creating custom reports in Power BI. It’s just that easy. I know this is not new, but really, we should start using this a lot more so that we can get in-depth reports about our devices in the organization.
Intune and Android Enterprise Management
In this session, some really great features are announced! Android Enterprise is evolving for sure. In Android Nougat (Android 7.0), we had the availability for Work Profiles in Android Enterprise, which we used a lot and worked great. Android Oreo (Android 8.0) took this even to a next level. Here you have a great overview of the new features each version.
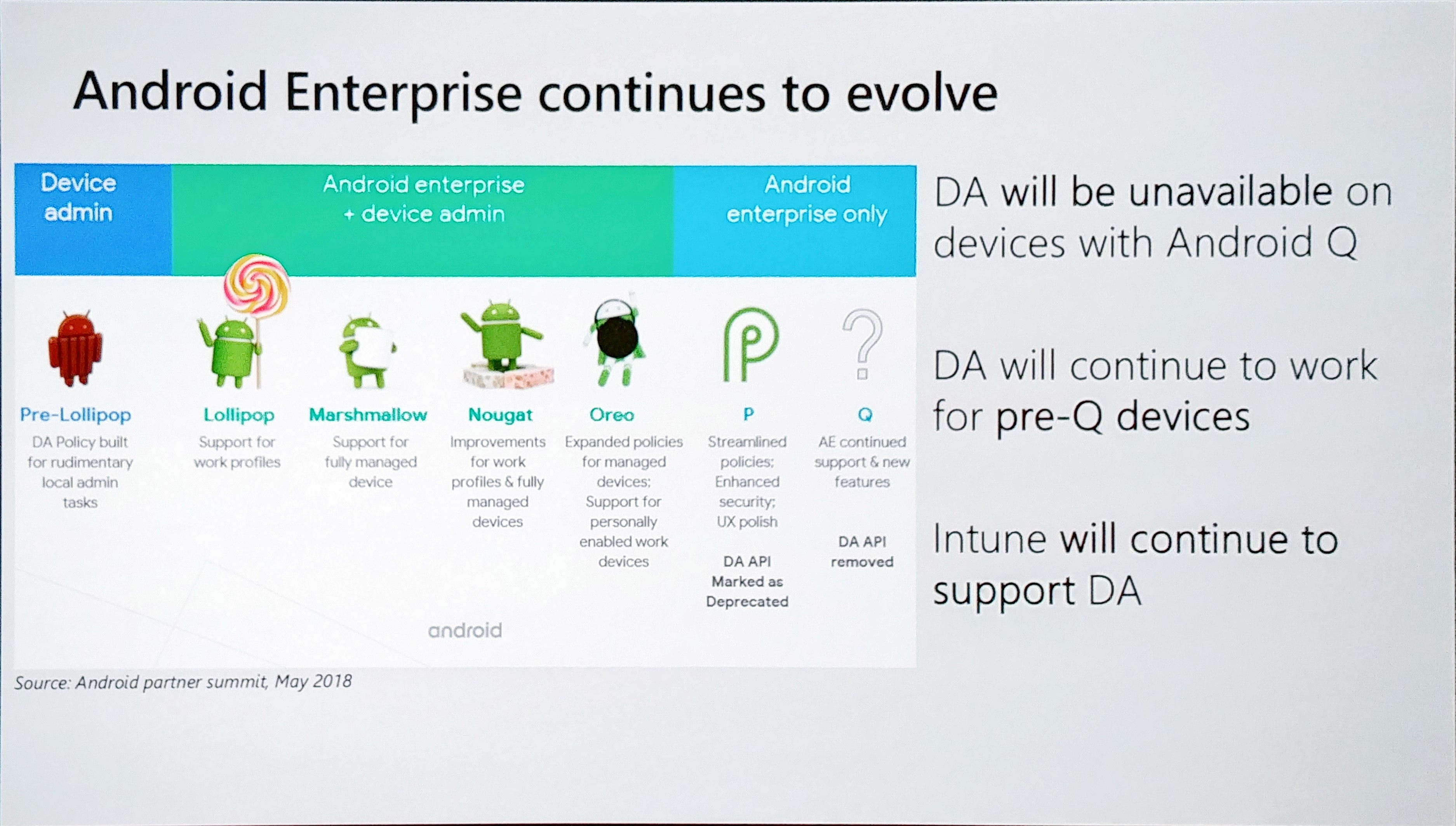
Google discourages non-Work Profile as well because it requires Device Admin for the Intune App. that means that if we use the android App Managed mode, the user needs to give Device Admin rights to the Intune app and it needs to go through a lot of “Accept” screens as well. That scares of the user and we want the opposite. So you should use the “Work Profile” in Android Enterprise in my opinion if you use BYOD. You can separate apps from personal in this mode, you even create containerized apps which means that you could prohibit copying work information to personal owned apps.
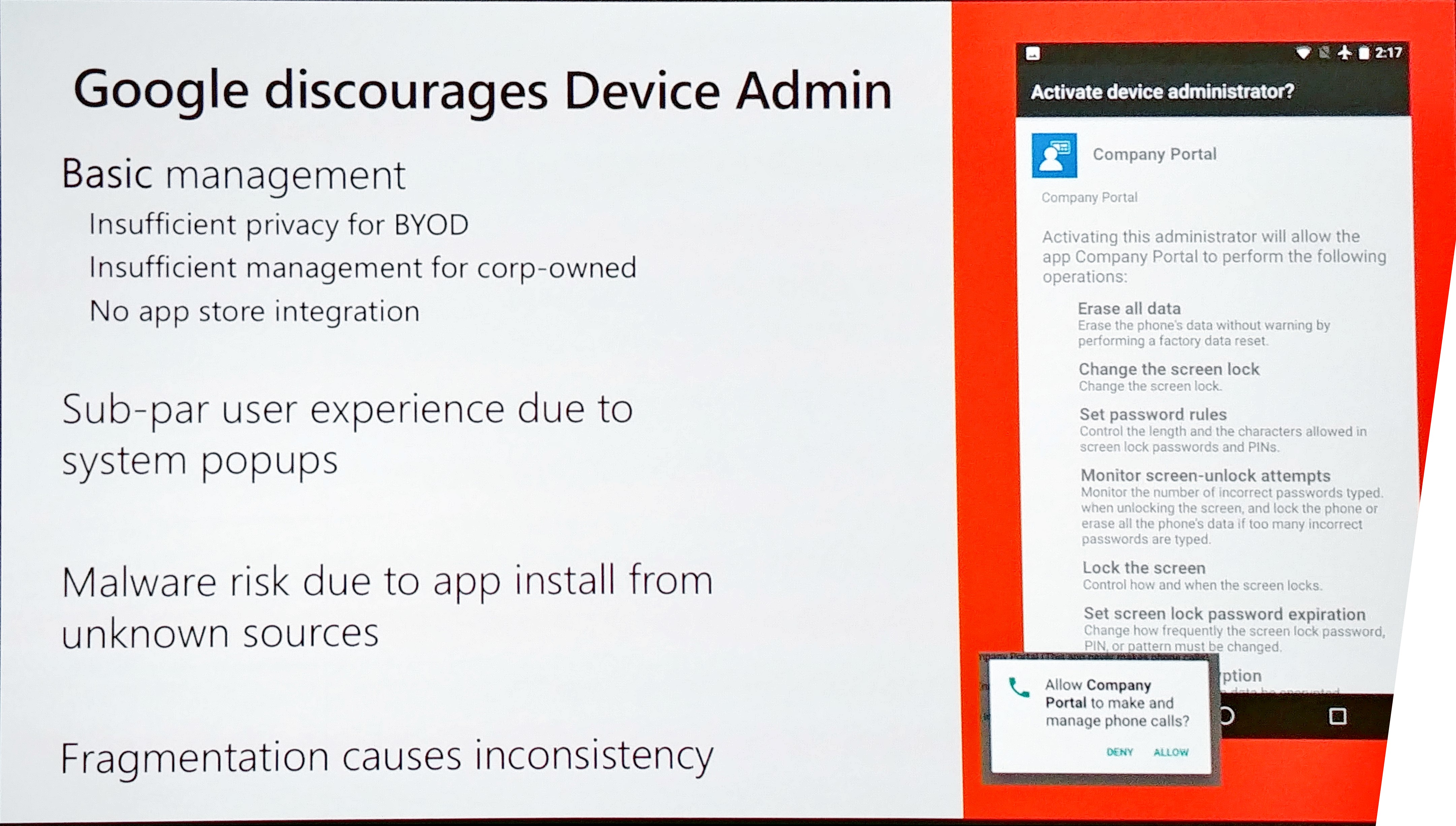
Now if you have corporate owned devices, you have three options and later this year, you have four. The third is Dedicated mode (it’s basically a kiosk mode). With Kiosk Mode, the user has no flexibility at all. It can only open the apps provided by the company. This is, however, very functional in certain security related scenario’s. The last one, Fully Managed, will be available for preview this year. This gives you great user experience and manageability, integrated with the Androind Management API (see next chapter).
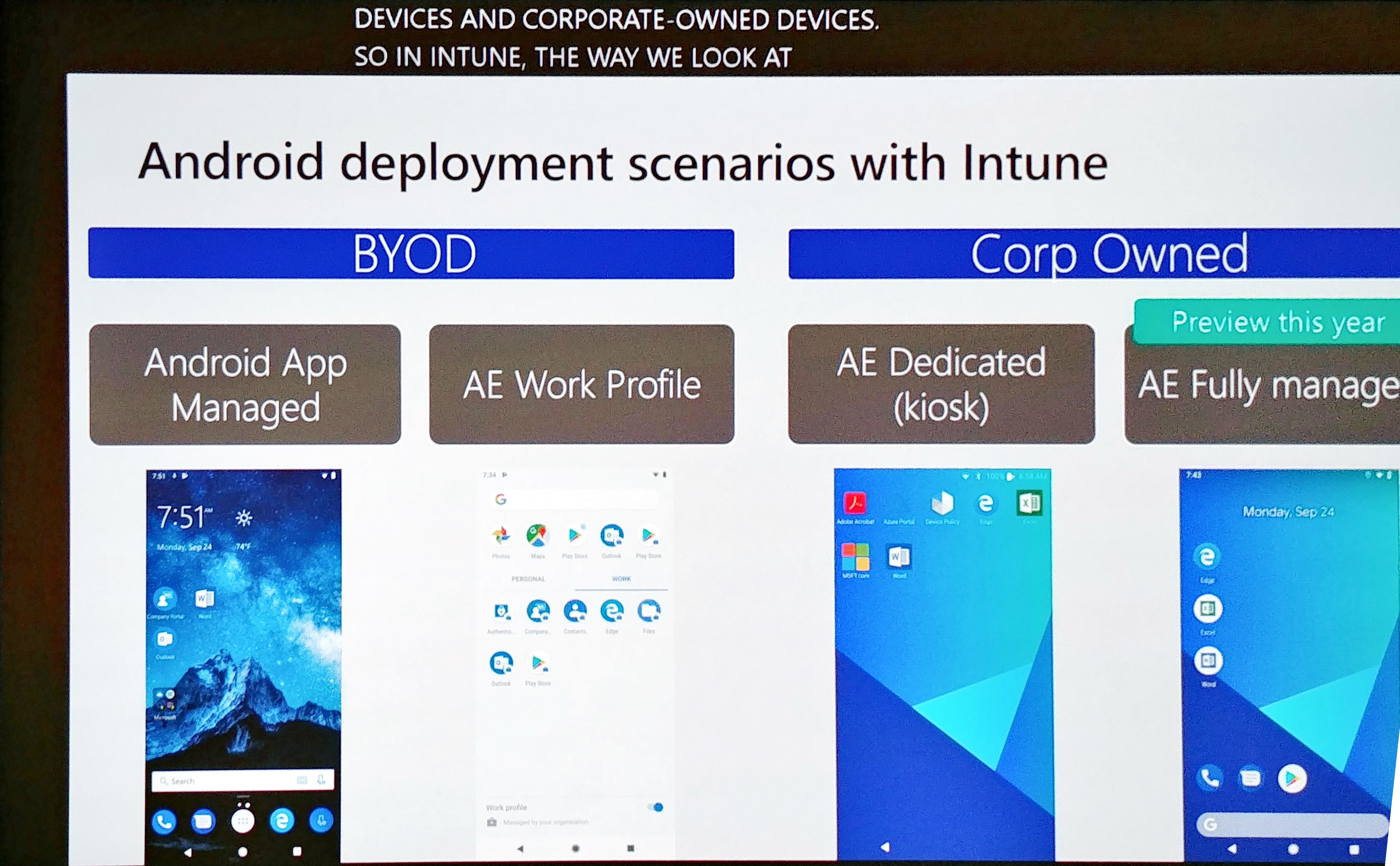
Android Management API
another great feature is that the Android Enterprise devices now communicate with the Android Management API. this means that Android and Intune can now provide updates and new functionalities at a speed that was never possible before.
I am getting a little bored if I read my blog again for readability if I keep saying: another great feature! But how do I say this else, here is another great feature, Managed Google Play! This provides mobile app management in Android Enterprise, including silent installs for required apps. We can also now control over what apps ends users can install in work context. In addition to this, we have the possibility to fully configure, for example the Outlook app, before it gets installed on the client device. The Managed Google Play will be available through the Intune Portal. No separate login necessary.
Google developed zero-touch with Intune. This is available with any Android Enterprise corp-owned deployment. This already works today with the dedicated device scenario and Android 8. This has some great feature updates however. If you go to https://partner.android.com, you can automatically assign a device to corporate policy and assigning a device to your company is going very smoothly. Check the screenshots below.
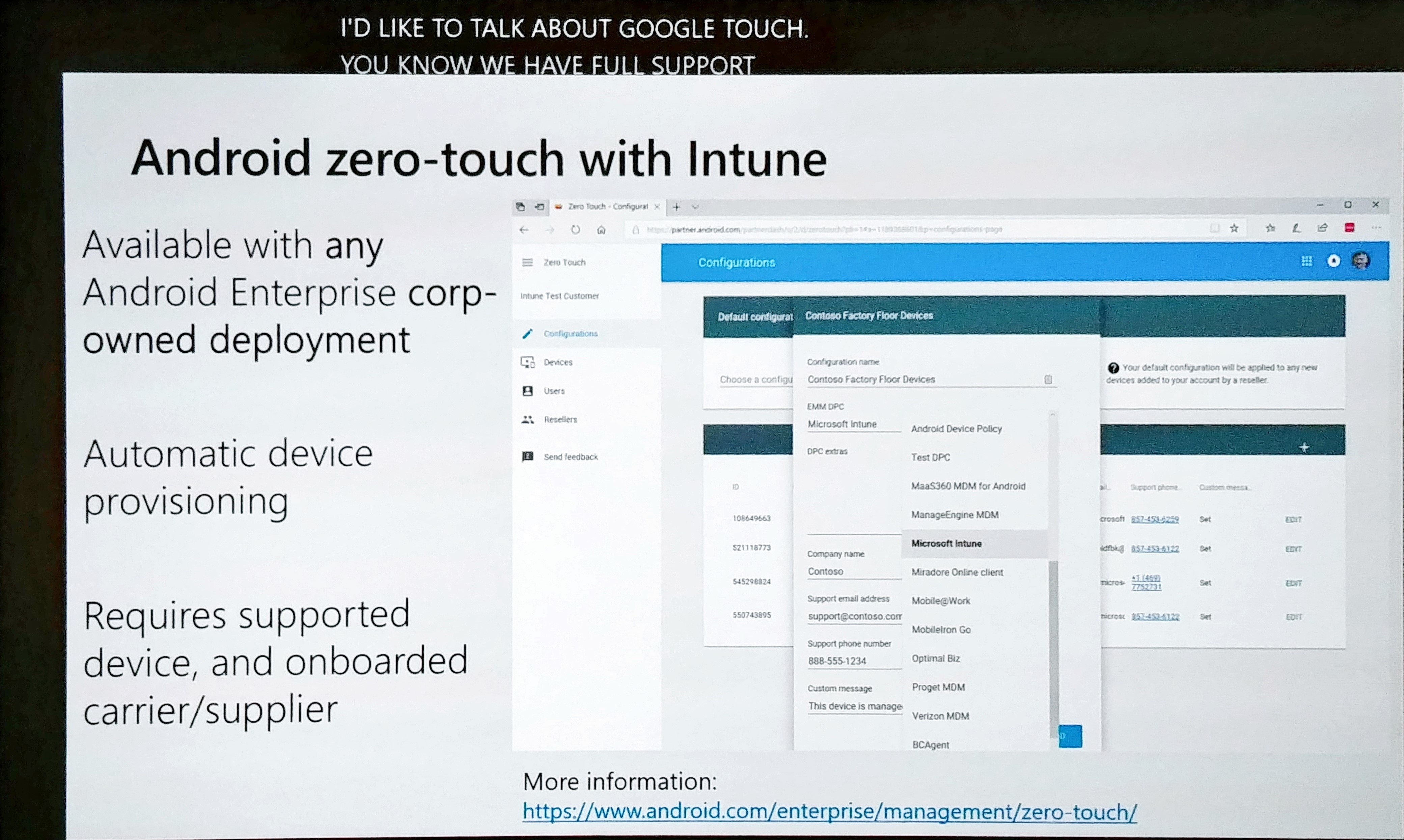
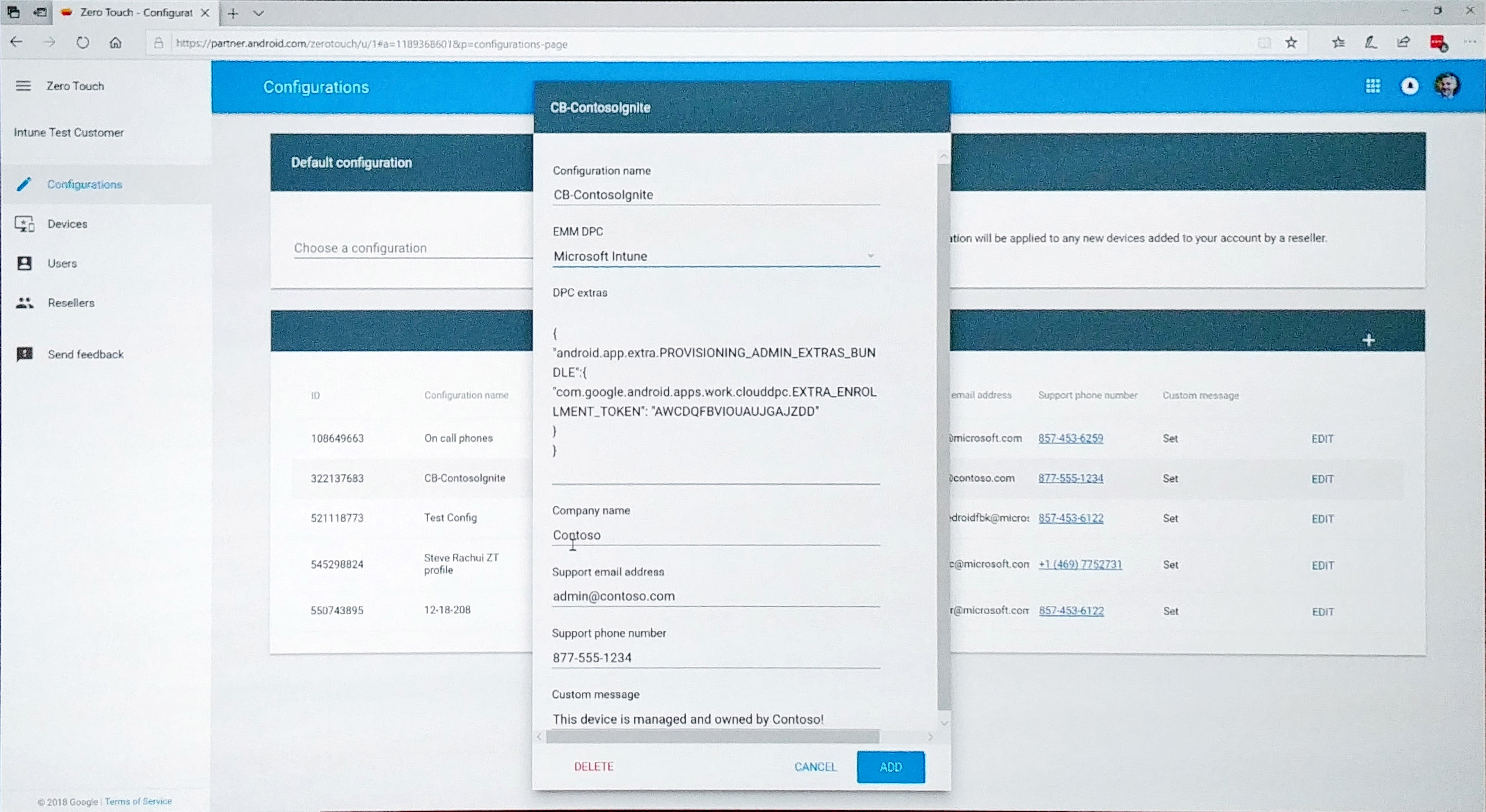
Integrated Information Protection in external sharing SharePoint and OneDrive
Wow, I never saw so many new features on such a relatively small part of a product. The session was 75 minutes but it didn’t bore me a minute! They received a big applause as well, so let’s start.
Smart People Picker and sharing
The first new feature we have this year is the Smart People Picker. If you share a link, you will be presented with suggestions of people that SharePoint thinks you want to share the document with. Machine learning is behind this so it will take some time to present you with the right results, but it will get there (if it’s not there already). This sharing experience will be exactly the same on mobile and the same experience is built in Microsoft Teams. Sharing capabilities supports branding now which is integrated with the Azure AD branding functionality. So if you already configured that, it will work right away, as soon as this feature is rolled-out globally.
Link Reminders
Another feature that we were actually missing (but didn’t realize I did miss it till now) is that if someone opens a link, we can get a confirmation email that the link is clicked. If you share a link, it’s possible that the receiver didn’t open the link yet. There is a 95% change that if the link isn’t opened in 7 days, it will never be opened. So now we can configure automatic reminders that tells you if the link is not opened yet. Another new feature is that you can set a custom message on the “request access” page if you are trying to access a specific site or document.
One-time passwords on link sharing
Link sharing has further improved security. You can configure a one-time password for opening a document. It’s great for reviewing and for making sure that the recipient can only watch it once. Also, we can set per site specific sharing setting. Currently, if you disable the “Anyone” sharing setting, it’s effective for your whole tenant. So now it’s possible to configure this per site.
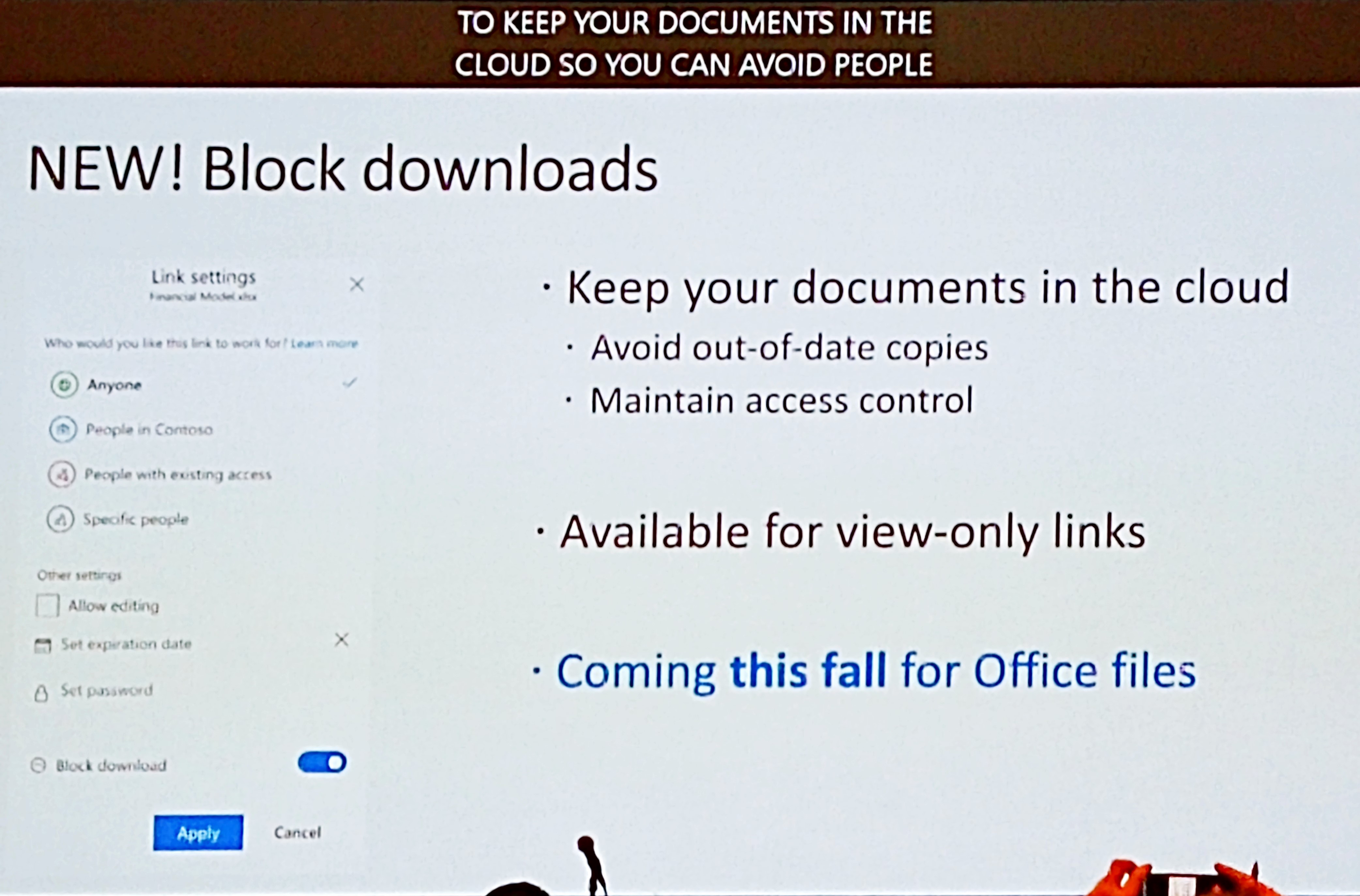
Block file downloads
The next feature is in my opinion the best feature. We can block downloads on a file and make it read only. With this new “Information Protection” possibility, we can fully control our documents and still collaborate in that same document. If you enable this setting, the file cannot be downloaded, printed, copied etc. Before, this was only possible if we classify documents and apply encryption. There was no other way of keeping control of your files. Now it’s possible without Azure Information Protection.
Collaboration improvements
Collaboration is an important part of our job every day and I am happy to tell you that collaboration in SharePoint and OneDrive is extended big time. For example if you are working in a PowerPoint presentation and you like having someone else checking your slide, you just mention someone at the side of the slide like you are used to be now. Use the @name format and the person will be notified by email immediately. This works for Office apps on Windows soon and will come later this year for MacOS as well.
In Microsoft Teams, we also have a new functionality. If we are uploading new files, we have the possibility to notify team members that you uploaded files.
Admin control settings enhancements
For the admin, we have more settings now we can control.

Expiring links for external access
And last but not least, we can set expiring links for external access! I think this is a really good feature because I get the question a lot: how can I keep control of shared files externally. Of course there are ways like Cloud App Security, make a person responsible for checking shared links etc. But why not just let the link expire? For example after 6 months? Sounds totally reasonable to me. If there is access needed after that time, you can just re-share the link.
Experiences with going password-less
Well, this one gave some new insights about the password-less world. Microsoft wants to get rid of passwords with good reasons, but it’s not that easy. Microsoft presents you with 4 simple steps:
- Implement Windows Hello For Business
- Reduce user-visible password surface area
- Transition into password-less deployment
- Eliminate password from identity directory
And this is all assuming that you can even make it to step 4. The biggest problem is with your on-premises apps. It can be very hard to transform these apps to password-less sign in so keep that into account. The non-marketing way of achieving this is a lot harder.
