Microsoft Ignite day 3
Azure AD Conditional Access
We have some great new features in Azure AD Conditional Access, they are really taking it to a next level. Conditional Access has now tight integration with Cloud App Security. It’s now possible to fully control and secure our data and information when you collaborate with a partner (B2B) or within your own tenant.
Index:
- Azure AD Conditional Access
- Cloud App Security integration with Windows Defender ATP
- Microsoft Secure Score
- Identity Protection
- Intune Updates
As you might probably now, Cloud App Security has tight integration with SharePoint already but now we can control on file level if a download for example is allowed or not. Check this screenshot below from the Ignite presentation:
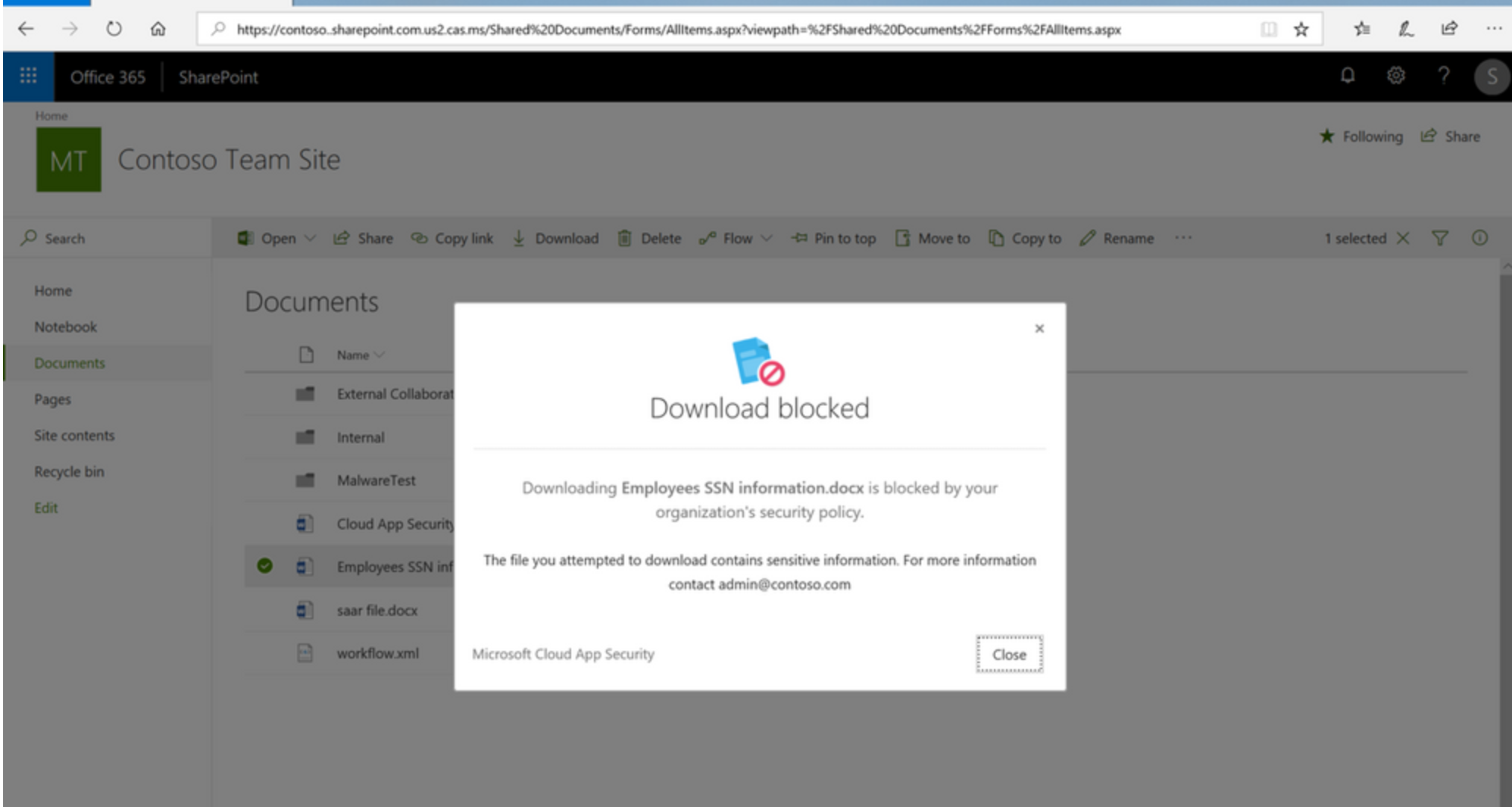
Another great update is that we can now enable Conditional Access App Control for Office applications. Before this was only possible with SAML-based apps. Based on the risk level of a user’s session, information can be accessed or blocked. Also risky OAuth applications can now be blocked with Cloud App Security. These updates make Cloud App Security even more powerful. If you aren’t using it right now, you should! It makes your organization a lot more secure.
Well, enough updates around Conditional Access right? It goes even further. We can not only control Exchange, but specific mailboxes within an account. The command runs as follows to enable this feature:
1 | Set-OwaMailboxPolicy –Identity user –ConditionalAccessPolicy $true |
This command does not work yet and to be honest, I am not sure what it will actually do as I cannot test it yet. But I expect we will have some sub-commands in the near future to further control this.
Cloud App Security integration with Windows Defender ATP
Cloud App Security is now integrated with Windows Defender ATP! At first, we needed to install a Cloud App Security client which was too much because we had already so many clients installed. So they came up with the Cloud App Security broker which was an improvement on the client side, but then we needed to proxy all our traffic through it. We now we have the best solution, integration with Windows Defender ATP! I personally love this because configuring a separate gateway is no longer necessary. All traffic can be routed through Defender ATP (and the Defender client is installed by default with Windows 10). This is a great way of securing your information and it makes controlling your devices very easy. Here you can see information is being fed from Windows Defender ATP.
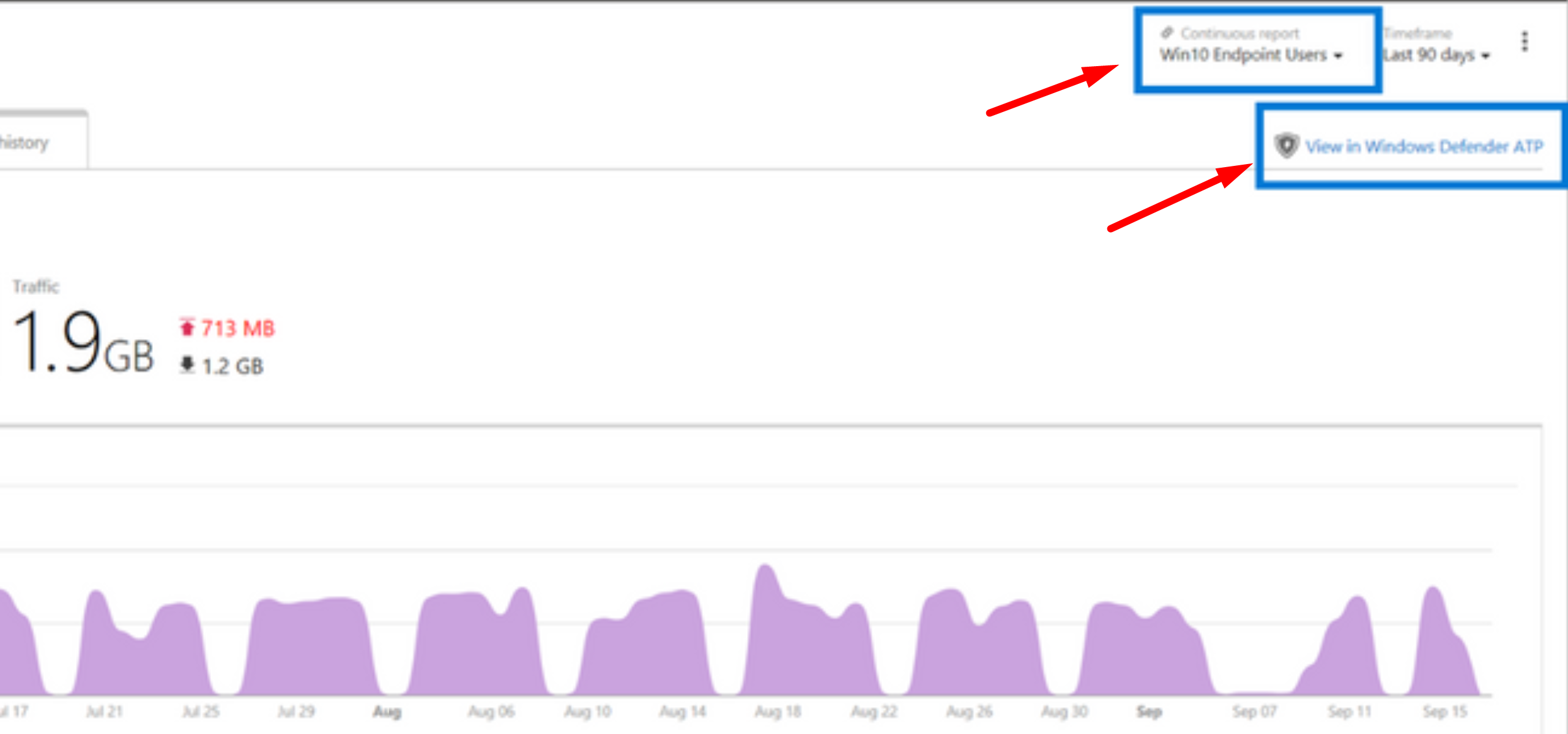
In Windows Defender ATP, you only have to enable this.
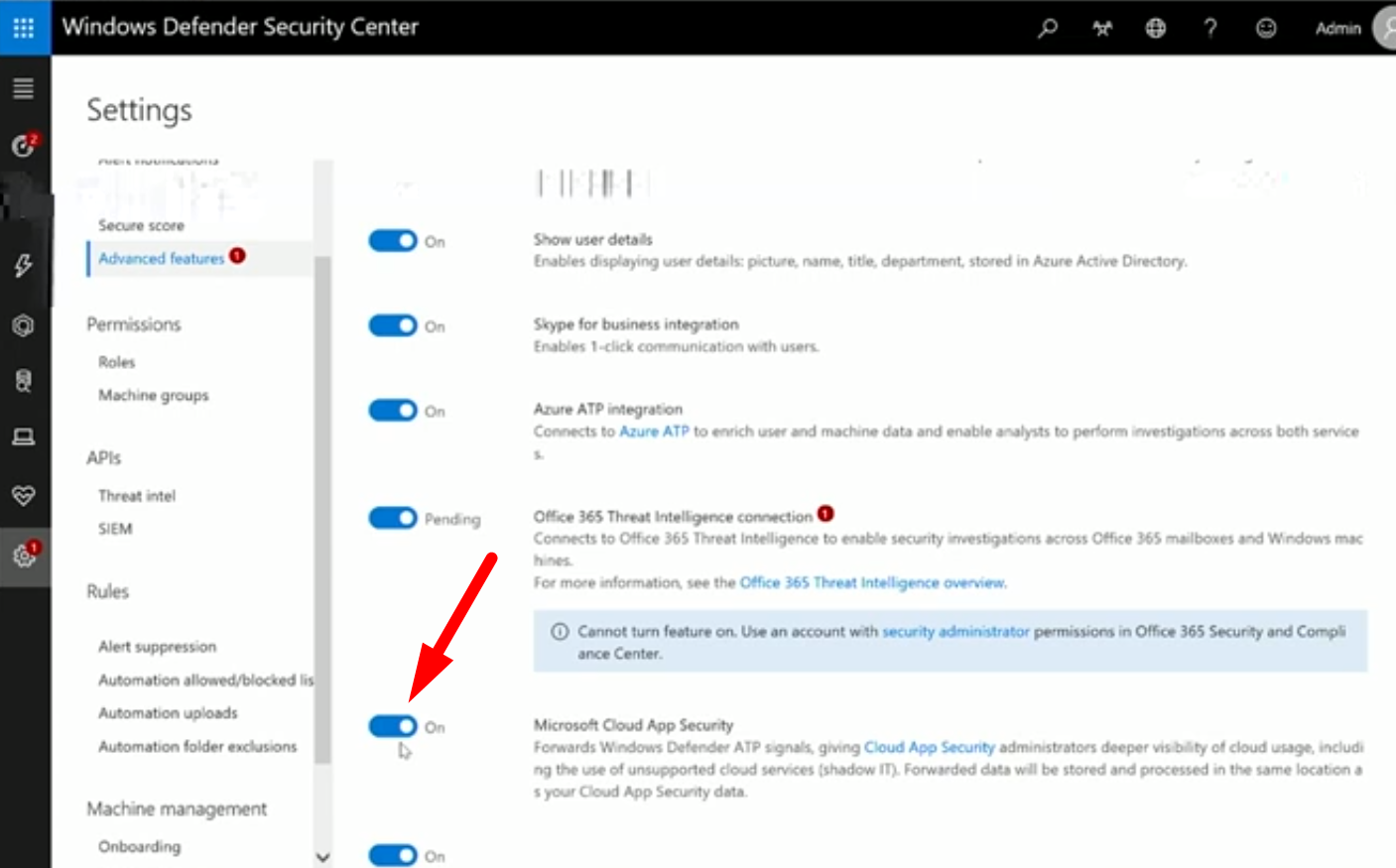
After enabling this setting, it will Cloud App Security feed traffic and device information from Windows Defender ATP.
Microsoft Secure Score
We have heard in almost every session that we should enable Microsoft Secure Score. I do agree that we should enable it on all our tenants (so I am telling you again now :)) and it is also enabled now through Azure Active Directory (you can go to https://securescore.microsoft.com/ as well). It looks like this:
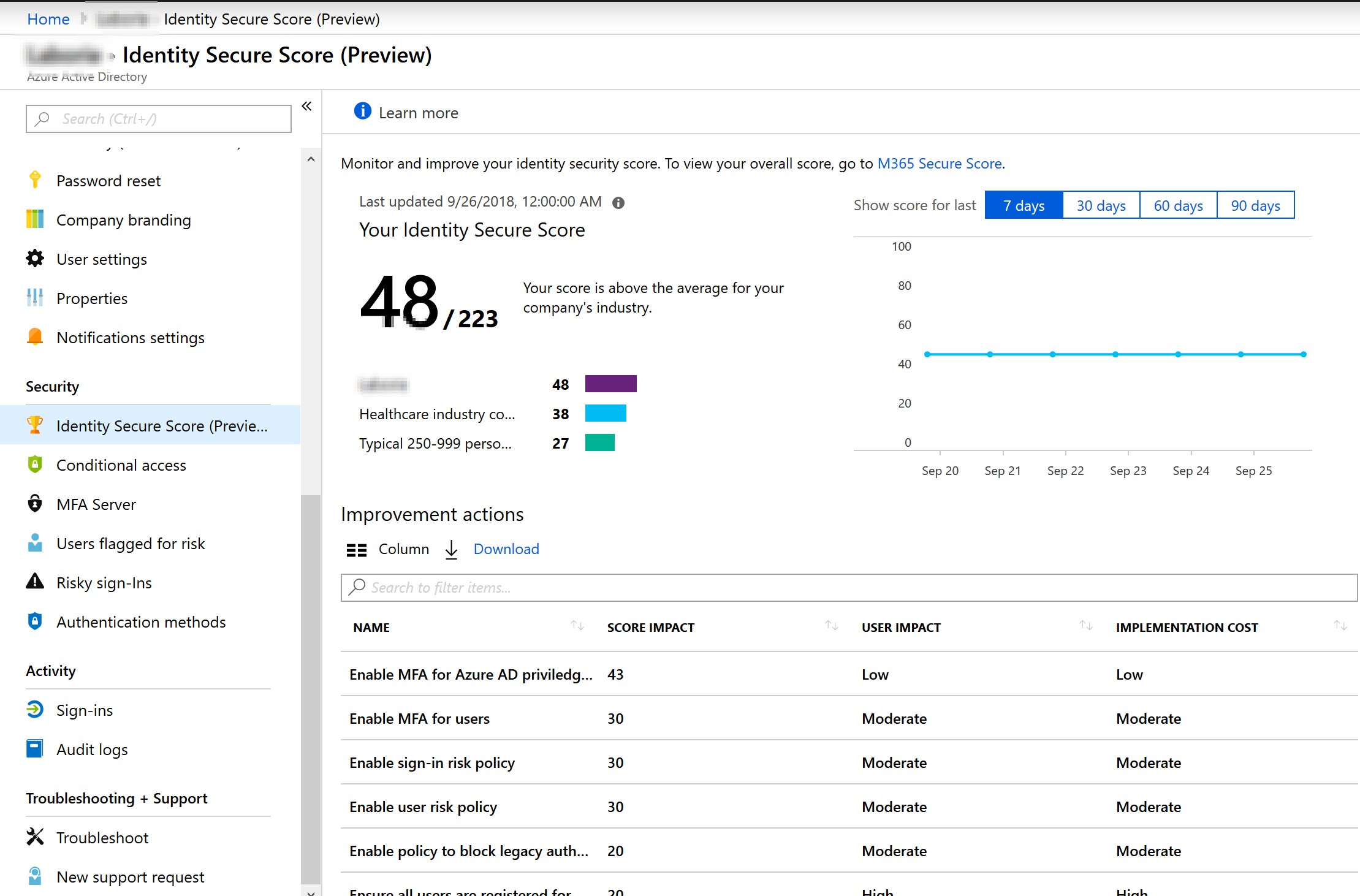
It looks good and it will only show the score that you have access too. Like if you don’t have EM+S E5, you won’t see identity protection related security scores.
Identity Protection
Identity Protection does now have integration with Azure ATP. Azure ATP is a security service based on DNS checks. Risky sign-ins from these two products can now be viewed from a single panel. And of course, we can apply conditional access on this. If Azure ATP feeds Identity Protection with a risky sign-on, it can be blocked, based on your Conditional Access settings. Combining these two sources, you have a very powerful solution. You see all high risk devices and users and all items that needs attention are presented through one combined interface.
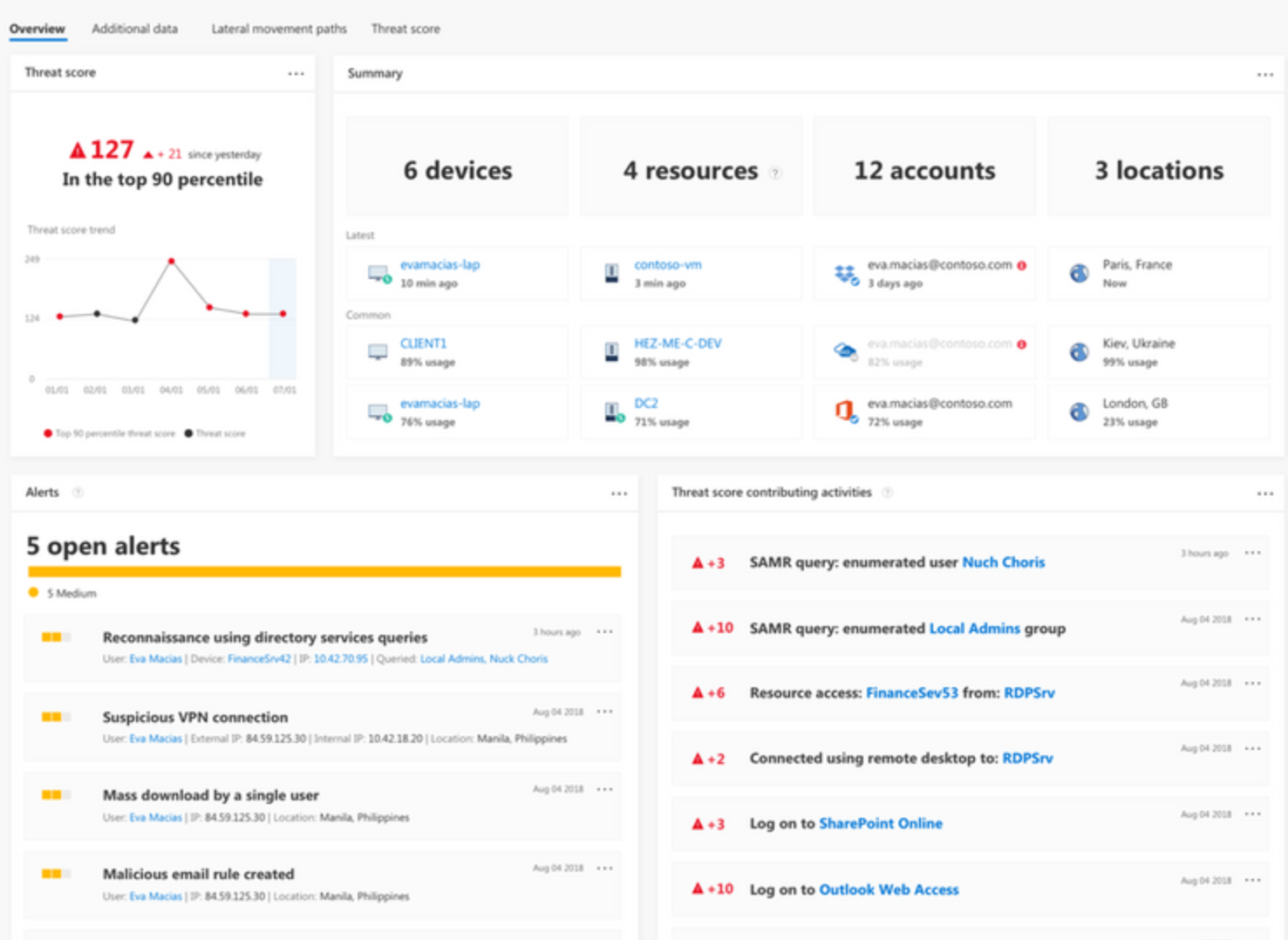
Intune updates
As you might know by now is that my main focus is within the “Information Protection” field which includes parts of Cloud App Security and Intune as well. So I wanted to post some updates around Intune, Windows Information Protection (which is part of Intune) and device management. That’s why I visited the session “What’s new in Windows 10 mobile device management (MDM)” . But right from the start I thought: Are we really going to do this for 75 minutes? I barely heard anything new and I love to share new stuff to the world. For example the presenter said that we should focus on co-management, 1 of 3 points she gave as a call-to-action. Isn’t this already possible for years now?
Also, we were presented slides like this:
Really? I want to see what’s NEW. Anyway, a little good news however, Kiosk mode control is now generally available and we will get better security baselines for Microsoft Intune. Maybe you have another opinion about this session, I would love to hear from you through comments below.
So this is basically it. We saw a lot of sessions but a lot of sessions presented content already covered in day 1 and 2. I don’t expect much more announcements in day 4 and 5. Maybe I will wrap them together in one blogpost, depending on the content of tomorrow.
But still, Ignite brought me definitely the sessions above expectations!
